Hack Windows 7 Password Step By Step Guide.
( “For Educational Purposes Only” ) - First of all start your Computer. When you see the start screen immediately power off your PC (Forced shut down).
- Start Your computer again. This time a message will appear saying , windows failed to start up.
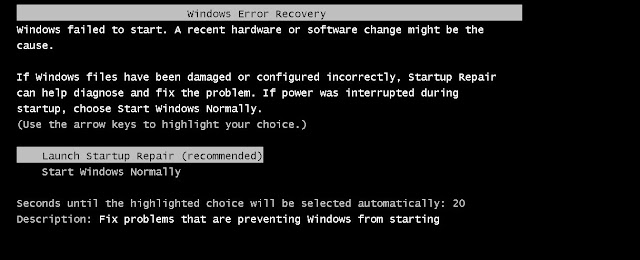
- Select the option , Launch start up repair (Recommended) and wait for few minutes.
- You will get option of system restore at this point of time.It will take few minutes.
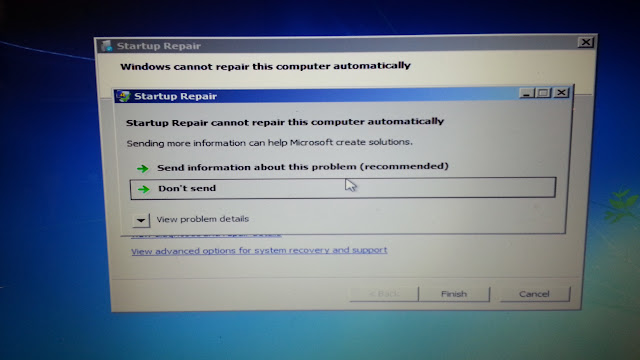
- Now, Press, View problem details (Click on downward arrow in the left ).Now scroll down all the way to the bottom of the page and you will find a .txt file as shown in Video.
- Just Click on that file and it will open the txt file in notepad.Now click on File and Then Open.
- Now navigate to the folder given below.
- Now Search for a file named setch.(setch allows you to open Ease To acess)
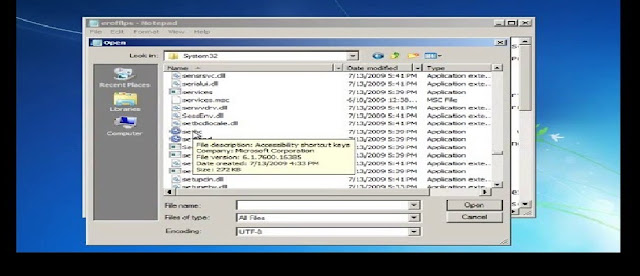
- Just rename it to setch-1 . (You can rename it back to original later)
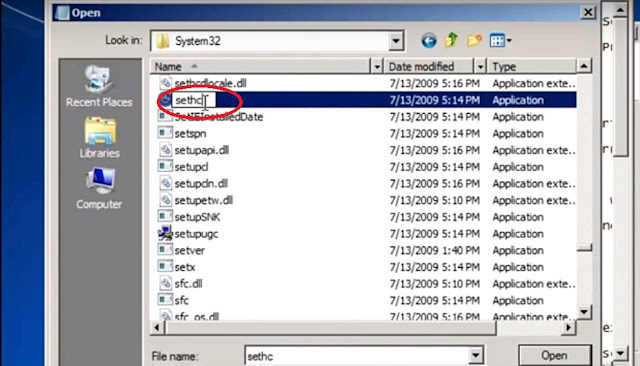
- Now find file named cmd.Just copy the file and paste it there (in same directory in which you are currently in) And ]rename this file cmd-copy as setch.
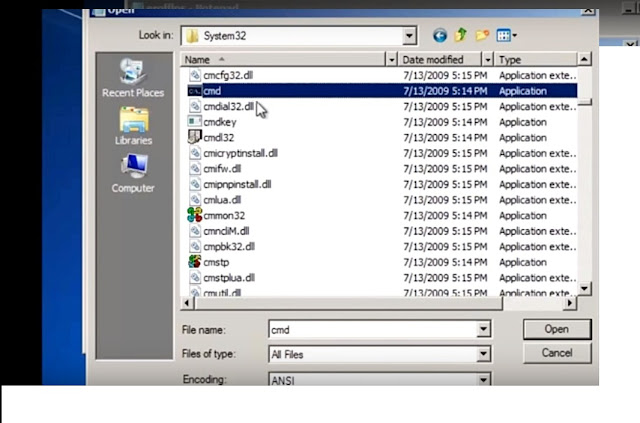
- Now close it And restart your computer.
- Once you reach the Log in Window, Just press shift key 5 times on your keyboard.This will open Cmd (Beacuse we changed sethc to cmd).
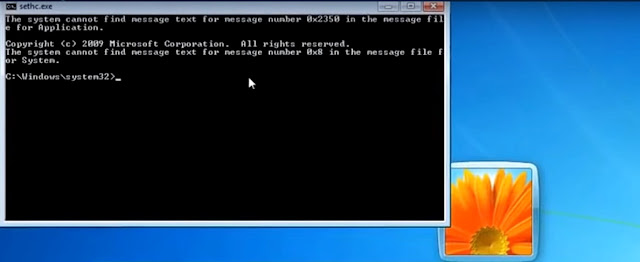
- Now type following commands carefully :
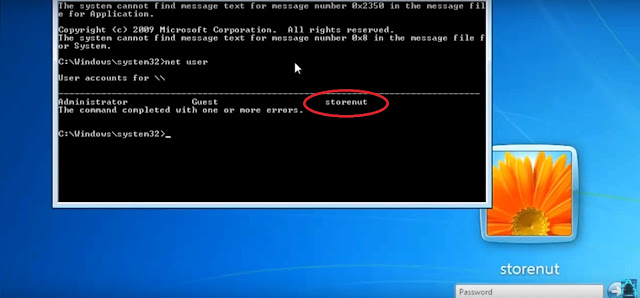
- This command will show all user including AdminNow you will see admin username. (Storenut in our case )
- Now type following command :
eg : net user Storenut * (because storenut is admin in our case )
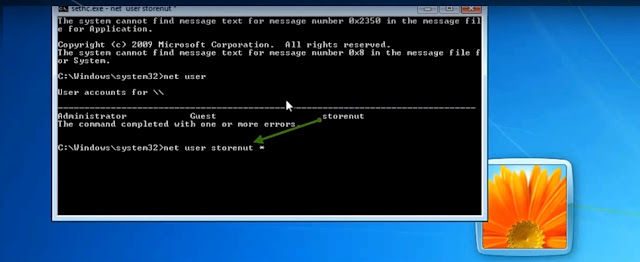
- This will ask you to type a password and retype password just hit enter both times.
Congrats Admin password removed!! .
Facebook’s integration with the Oculus virtual reality headset could have opened doors for malicious attackers to hijack accounts by exploiting the latter had the social networking giant not patched the vulnerabilities.
Oculus, known best for their Oculus Rift virtual reality (VR) headset, was founded in 2012. In March 2014, Facebook announced that they would acquire Oculus VR, which was later completed in July 2014. In August 2014, Facebook included Oculus Rift in its white hat bug bounty program and paid money to researchers for reporting bugs. Since then, several vulnerabilities have been found in Oculus services including a series of flaws that earned a researcher $25,000.
In October 2017, Josip Franjkovic, a web security consultant, decided to examine the Oculus application for Windows, which enables users to connect their Facebook accounts for a more social experience by using both the native Windows Oculus application and browsers.
In his research, Franjkovic demonstrated how an attacker could hijack Facebook accounts by using specially crafted GraphQL queries to connect a victim’s Facebook account to the attacker’s Oculus account and obtain the victim’s access_token, which also has access to Facebook’s GraphQL endpoint. Using specially crafted GraphQL queries, the attacker can take control of the victim’s Facebook account and change the victim’s account’s phone number and then reset the account’s password.
Franjkovic reported the vulnerability to Facebook on October 24 under the company’s bug bounty program for which a temporary fix was done on the same day that involved disabling the facebook_login_sso endpoint. Further, a permanent patch was rolled out by Facebook on October 30.
However, Franjkovic discovered a login CSRF (cross site request forgery) vulnerability a few weeks later that could have been used to exploit bypass Facebook’s patch by redirecting the victim to an Oculus URL of the attacker’s choice.


Franjkovic reported the second flaw to Facebook on November 18 for which a temporary fix was done on the same day by again disabling thefacebook_login_sso endpoint. Three weeks later, a complete patch was rolled out by the company.
“The fix was to implement a CSRF check on the /account_receivable/endpoint, AND add an additional click to confirm the link between Facebook and Oculus accounts,” Franjkovic wrote. “I believe this properly fixes the vulnerability without degrading user experience too much.”
While Franjkovic did not disclose how much bounty amount he earned from Facebook for discovering the vulnerabilities, but the social networking giant did reveal last week (via SecurityWeek) that it had ended up paying $880,000 in bug bounties in 2017 to security researchers.













